Security
Of course, IsarFlow permits a security view on your network. Computers infected by worms and viruses are easy to identify in systematic order. Because, in contrast to an application, a worm does not 'know' the LAN and is disclosed by its network scans.
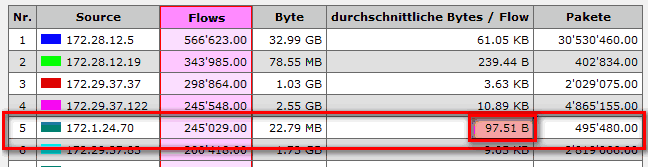
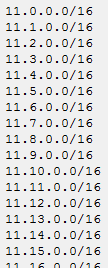
The first three machines in following analysis address a conspicuously high amount of /16 subnets.
In other words, these computers send their requests to more than one third of the entire IPv4 space in only one hour.
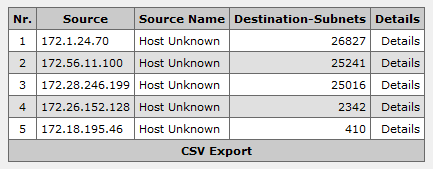
A first glance at the details shows obviously, this host initiates systematic network scans.
A drill-down indicates multitudes of 'midget data' flows.
Even short DNS queries are bigger than the shown flow sizes...
Additional analyses reveal: This computer scans others hosts over the Windows filesharing ports.
The immediate action would be to either remove the machine from the network or at least to inform the responsible administrator.